Create Your Own VPN Server
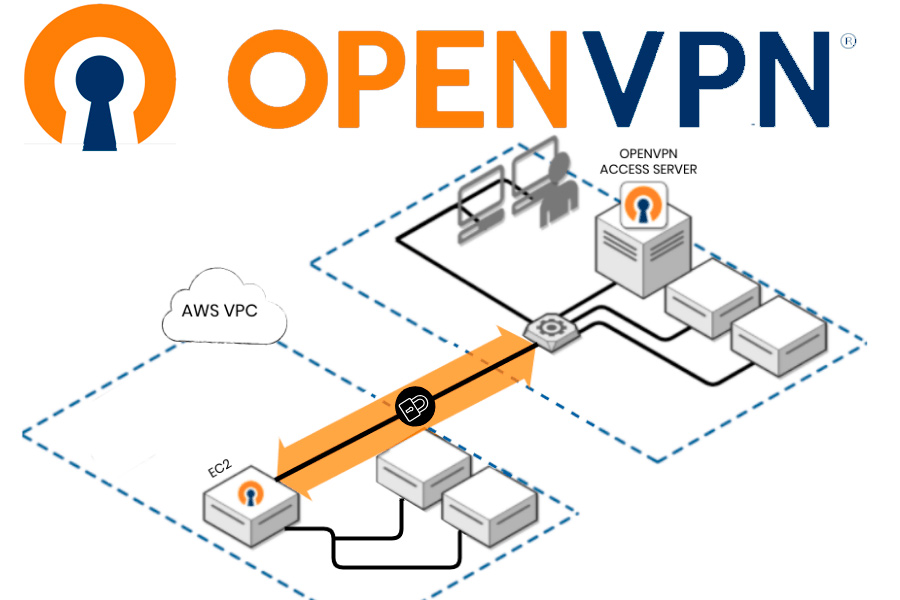 OpenVPN is a free software-based connectivity tool: SSL, VPN Virtual Private Network. OpenVPN offers point-to-point connectivity with hierarchical validation of remotely connected users and hosts.
OpenVPN is a free software-based connectivity tool: SSL, VPN Virtual Private Network. OpenVPN offers point-to-point connectivity with hierarchical validation of remotely connected users and hosts.
 OpenVPN is a free software-based connectivity tool: SSL, VPN Virtual Private Network. OpenVPN offers point-to-point connectivity with hierarchical validation of remotely connected users and hosts.
OpenVPN is a free software-based connectivity tool: SSL, VPN Virtual Private Network. OpenVPN offers point-to-point connectivity with hierarchical validation of remotely connected users and hosts.
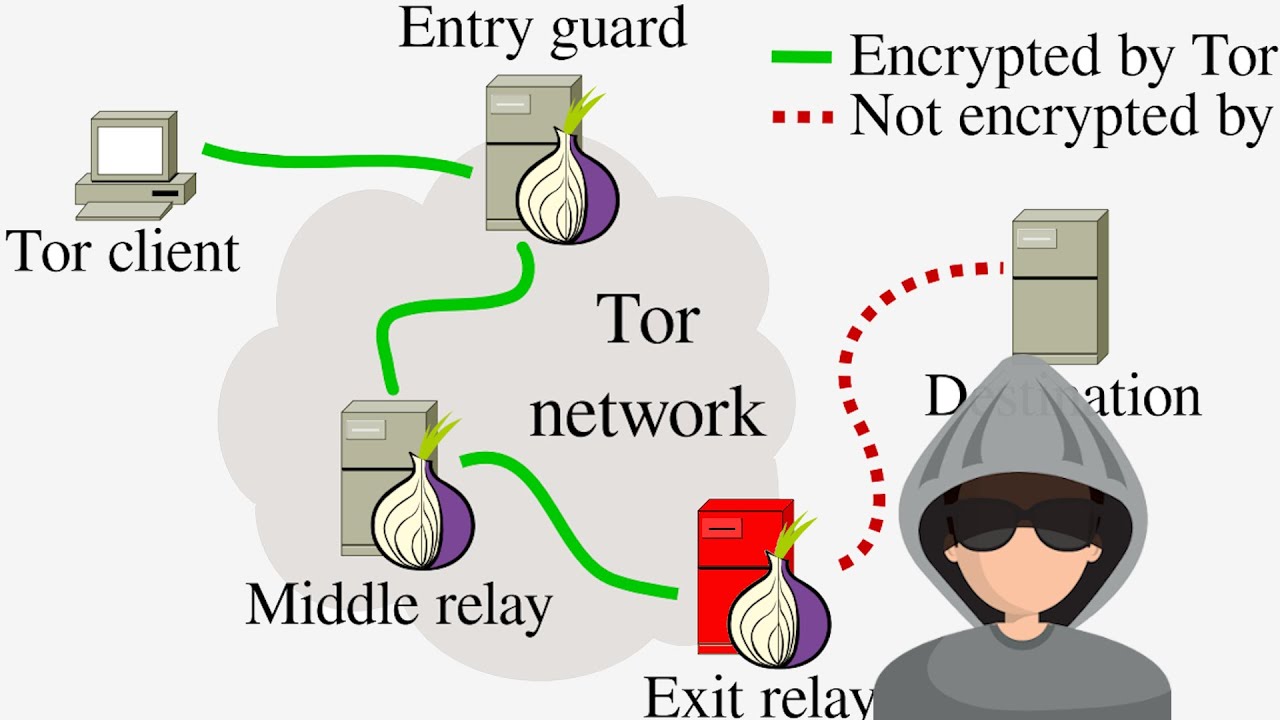 The Tor network depends on volunteers who donate bandwidth. The more people keep repeaters running, the Tor network will be better. Today’s Tor network is quite small compared to the number of people who need to use it, which means we need more volunteers like you to launch repeaters.
The Tor network depends on volunteers who donate bandwidth. The more people keep repeaters running, the Tor network will be better. Today’s Tor network is quite small compared to the number of people who need to use it, which means we need more volunteers like you to launch repeaters.
 Whonix is an operating system that utilizes top level security research and best practices to help users stay anonymous on the internet. To protect a user’s anonymity on the Internet on the technological level Whonix uses virtualization and the Whonix-Workstation combined with the Whonix-Gateway to force all connections through the Tor network.
Whonix is an operating system that utilizes top level security research and best practices to help users stay anonymous on the internet. To protect a user’s anonymity on the Internet on the technological level Whonix uses virtualization and the Whonix-Workstation combined with the Whonix-Gateway to force all connections through the Tor network.
 Proxychains-ng is a proxy server that supports HTTP, SOCKS4 and SOCKS5 internet protocols, and that works on Linux / GNU, BSD and Mac OS X distributions. Proxychains-ng allows any TCP connection made by a given program to follow a series of proxies up your destiny. In today’s post, we are going to cover the installation, configuration and usage of proxychains in kali linux.
Proxychains-ng is a proxy server that supports HTTP, SOCKS4 and SOCKS5 internet protocols, and that works on Linux / GNU, BSD and Mac OS X distributions. Proxychains-ng allows any TCP connection made by a given program to follow a series of proxies up your destiny. In today’s post, we are going to cover the installation, configuration and usage of proxychains in kali linux.
 The Tor network depends on volunteers who donate bandwidth. The more people keep repeaters running, the Tor network will be better. Today’s Tor network is quite small compared to the number of people who need to use it, which means we need more volunteers like you to launch repeaters.
The Tor network depends on volunteers who donate bandwidth. The more people keep repeaters running, the Tor network will be better. Today’s Tor network is quite small compared to the number of people who need to use it, which means we need more volunteers like you to launch repeaters.
 Whonix is an operating system that utilizes top level security research and best practices to help users stay anonymous on the internet. To protect a user’s anonymity on the Internet on the technological level Whonix uses virtualization and the Whonix-Workstation combined with the Whonix-Gateway to force all connections through the Tor network.
Whonix is an operating system that utilizes top level security research and best practices to help users stay anonymous on the internet. To protect a user’s anonymity on the Internet on the technological level Whonix uses virtualization and the Whonix-Workstation combined with the Whonix-Gateway to force all connections through the Tor network.
 Proxychains-ng is a proxy server that supports HTTP, SOCKS4 and SOCKS5 internet protocols, and that works on Linux / GNU, BSD and Mac OS X distributions. Proxychains-ng allows any TCP connection made by a given program to follow a series of proxies up your destiny. In today’s post, we are going to cover the installation, configuration and usage of proxychains in kali linux.
Proxychains-ng is a proxy server that supports HTTP, SOCKS4 and SOCKS5 internet protocols, and that works on Linux / GNU, BSD and Mac OS X distributions. Proxychains-ng allows any TCP connection made by a given program to follow a series of proxies up your destiny. In today’s post, we are going to cover the installation, configuration and usage of proxychains in kali linux.
 The eCPPT designation stands for eLearnSecurity Certified Professional Penetration Tester. eCPPT is a 100% practical and highly respected Ethical Hacking and Penetration Testing Professional certification counting certified professional in all the seven continents.
The eCPPT designation stands for eLearnSecurity Certified Professional Penetration Tester. eCPPT is a 100% practical and highly respected Ethical Hacking and Penetration Testing Professional certification counting certified professional in all the seven continents.
 VMware is a software company that provides virtualization and cloud computing software and services. Virtualization technology allows multiple operating systems to run on a single physical computer, enabling hardware resources to be shared among multiple virtual machines. This technology helps businesses to reduce costs by increasing server utilization, consolidating servers, and reducing power consumption.
VMware is a software company that provides virtualization and cloud computing software and services. Virtualization technology allows multiple operating systems to run on a single physical computer, enabling hardware resources to be shared among multiple virtual machines. This technology helps businesses to reduce costs by increasing server utilization, consolidating servers, and reducing power consumption.

 ¡Welcome to my webpage! Amazing things are about to come.
¡Welcome to my webpage! Amazing things are about to come.

 You have been assigned to a client that wants a penetration test conducted on an environment due to be released to production in seven days. The client requests that an engineer conducts an assessment of the provided virtual environment. The client has asked that minimal information be provided about the assessment, wanting the engagement conducted from the eyes of a malicious actor (black box penetration test). The client has asked that you secure two flags (no location provided) as proof of exploitation.
You have been assigned to a client that wants a penetration test conducted on an environment due to be released to production in seven days. The client requests that an engineer conducts an assessment of the provided virtual environment. The client has asked that minimal information be provided about the assessment, wanting the engagement conducted from the eyes of a malicious actor (black box penetration test). The client has asked that you secure two flags (no location provided) as proof of exploitation.

 You have been assigned to a client that wants a penetration test conducted on an environment due to be released to production in seven days. The client requests that an engineer conducts an assessment of the provided virtual environment. The client has asked that minimal information be provided about the assessment, wanting the engagement conducted from the eyes of a malicious actor (black box penetration test). The client has asked that you secure two flags (no location provided) as proof of exploitation.
You have been assigned to a client that wants a penetration test conducted on an environment due to be released to production in seven days. The client requests that an engineer conducts an assessment of the provided virtual environment. The client has asked that minimal information be provided about the assessment, wanting the engagement conducted from the eyes of a malicious actor (black box penetration test). The client has asked that you secure two flags (no location provided) as proof of exploitation.

 You have been assigned to a client that wants a penetration test conducted on an environment due to be released to production in seven days. The client requests that an engineer conducts an assessment of the provided virtual environment. The client has asked that minimal information be provided about the assessment, wanting the engagement conducted from the eyes of a malicious actor (black box penetration test). The client has asked that you secure two flags (no location provided) as proof of exploitation.
You have been assigned to a client that wants a penetration test conducted on an environment due to be released to production in seven days. The client requests that an engineer conducts an assessment of the provided virtual environment. The client has asked that minimal information be provided about the assessment, wanting the engagement conducted from the eyes of a malicious actor (black box penetration test). The client has asked that you secure two flags (no location provided) as proof of exploitation.

 You have been assigned to a client that wants a penetration test conducted on an environment due to be released to production in seven days. The client requests that an engineer conducts an assessment of the provided virtual environment. The client has asked that minimal information be provided about the assessment, wanting the engagement conducted from the eyes of a malicious actor (black box penetration test). The client has asked that you secure two flags (no location provided) as proof of exploitation.
You have been assigned to a client that wants a penetration test conducted on an environment due to be released to production in seven days. The client requests that an engineer conducts an assessment of the provided virtual environment. The client has asked that minimal information be provided about the assessment, wanting the engagement conducted from the eyes of a malicious actor (black box penetration test). The client has asked that you secure two flags (no location provided) as proof of exploitation.
 The eLearnSecurity Junior Penetration Tester (eJPTv2) is a 100% practical certification on penetration testing and information security essentials. By passing the exam, a cyber security professional proves to employers they are ready for a rewarding new career.
The eLearnSecurity Junior Penetration Tester (eJPTv2) is a 100% practical certification on penetration testing and information security essentials. By passing the exam, a cyber security professional proves to employers they are ready for a rewarding new career.
 Link-Local Multicast Name Resolution (LLMNR) and NetBIOS Name Service (NBT-NS) are two name resolution services that Windows machines use to identify host addresses on a network when DNS resolution fails. LLMNR and NetBIOS are enabled by default on modern Windows computers.
Link-Local Multicast Name Resolution (LLMNR) and NetBIOS Name Service (NBT-NS) are two name resolution services that Windows machines use to identify host addresses on a network when DNS resolution fails. LLMNR and NetBIOS are enabled by default on modern Windows computers.
 Link-Local Multicast Name Resolution (LLMNR) and NetBIOS Name Service (NBT-NS) are two name resolution services that Windows machines use to identify host addresses on a network when DNS resolution fails. LLMNR and NetBIOS are enabled by default on modern Windows computers.
Link-Local Multicast Name Resolution (LLMNR) and NetBIOS Name Service (NBT-NS) are two name resolution services that Windows machines use to identify host addresses on a network when DNS resolution fails. LLMNR and NetBIOS are enabled by default on modern Windows computers.
 Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user.
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user.
 Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user.
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user.
 VMware is a software company that provides virtualization and cloud computing software and services. Virtualization technology allows multiple operating systems to run on a single physical computer, enabling hardware resources to be shared among multiple virtual machines. This technology helps businesses to reduce costs by increasing server utilization, consolidating servers, and reducing power consumption.
VMware is a software company that provides virtualization and cloud computing software and services. Virtualization technology allows multiple operating systems to run on a single physical computer, enabling hardware resources to be shared among multiple virtual machines. This technology helps businesses to reduce costs by increasing server utilization, consolidating servers, and reducing power consumption.
 The eLearnSecurity Web Application Penetration Tester certification assesses a cyber security professional’s web application penetration testing skills. The exam is a skills-based test that requires candidates to perform a real-world web app pentesting simulation.
The eLearnSecurity Web Application Penetration Tester certification assesses a cyber security professional’s web application penetration testing skills. The exam is a skills-based test that requires candidates to perform a real-world web app pentesting simulation.
![]() This project will turn your Wi-Fi dev board into an open access point. When users try to connect to this access point they will be served a fake login screen. User credentials are sent to the Flipper and logged on the SD card.
This project will turn your Wi-Fi dev board into an open access point. When users try to connect to this access point they will be served a fake login screen. User credentials are sent to the Flipper and logged on the SD card.
 The OSCP is a hands-on penetration testing certification, requiring holders to successfully attack and penetrate various live machines in a safe lab environment. It is considered more technical than other ethical hacking certifications, and is one of the few certifications that requires evidence of practical penetration testing skills.
The OSCP is a hands-on penetration testing certification, requiring holders to successfully attack and penetrate various live machines in a safe lab environment. It is considered more technical than other ethical hacking certifications, and is one of the few certifications that requires evidence of practical penetration testing skills.
![]() Starting from the basics deepen your expertise in AWS security with a comprehensive exploration of advanced concepts, including in-depth identity and access management strategies, encryption methods, sophisticated networking defenses and learn how to spot and exploit misconfigurations in more than 20 common AWS services. Master the application of specialized red team and whitebox tactics in AWS contexts, enabling the detection and correction of complex security flaws.
Starting from the basics deepen your expertise in AWS security with a comprehensive exploration of advanced concepts, including in-depth identity and access management strategies, encryption methods, sophisticated networking defenses and learn how to spot and exploit misconfigurations in more than 20 common AWS services. Master the application of specialized red team and whitebox tactics in AWS contexts, enabling the detection and correction of complex security flaws.
![]() Starting from the basics deepen your expertise in AWS security with a comprehensive exploration of advanced concepts, including in-depth identity and access management strategies, encryption methods, sophisticated networking defenses and learn how to spot and exploit misconfigurations in more than 20 common AWS services. Master the application of specialized red team and whitebox tactics in AWS contexts, enabling the detection and correction of complex security flaws.
Starting from the basics deepen your expertise in AWS security with a comprehensive exploration of advanced concepts, including in-depth identity and access management strategies, encryption methods, sophisticated networking defenses and learn how to spot and exploit misconfigurations in more than 20 common AWS services. Master the application of specialized red team and whitebox tactics in AWS contexts, enabling the detection and correction of complex security flaws.
![]() Welcome to the review of SkullNet, my first CTF available out there, you have what it takes to solve it and become a SkullOperator? Show your skills in this CTF and retrieve the secret Flag!
Welcome to the review of SkullNet, my first CTF available out there, you have what it takes to solve it and become a SkullOperator? Show your skills in this CTF and retrieve the secret Flag!
![]() Welcome to the review of SkullNet, my first CTF available out there, you have what it takes to solve it and become a SkullOperator? Show your skills in this CTF and retrieve the secret Flag!
Welcome to the review of SkullNet, my first CTF available out there, you have what it takes to solve it and become a SkullOperator? Show your skills in this CTF and retrieve the secret Flag!
![]() Deepen your GCP security expertise from the basics to advanced levels, starting by exploring identity management, encryption, and networking defenses. Learn to identify and exploit misconfigurations in tens of the most used GCP services. Master specialized Red Team and Whitebox tactics tailored for GCP, enhancing your ability to detect and correct complex security flaws. Moreover, gain insights into red teaming within Google Workspace and discover effective strategies for pivoting between GCP and Google Workspace platforms.
Deepen your GCP security expertise from the basics to advanced levels, starting by exploring identity management, encryption, and networking defenses. Learn to identify and exploit misconfigurations in tens of the most used GCP services. Master specialized Red Team and Whitebox tactics tailored for GCP, enhancing your ability to detect and correct complex security flaws. Moreover, gain insights into red teaming within Google Workspace and discover effective strategies for pivoting between GCP and Google Workspace platforms.
![]() Deepen your GCP security expertise from the basics to advanced levels, starting by exploring identity management, encryption, and networking defenses. Learn to identify and exploit misconfigurations in tens of the most used GCP services. Master specialized Red Team and Whitebox tactics tailored for GCP, enhancing your ability to detect and correct complex security flaws. Moreover, gain insights into red teaming within Google Workspace and discover effective strategies for pivoting between GCP and Google Workspace platforms.
Deepen your GCP security expertise from the basics to advanced levels, starting by exploring identity management, encryption, and networking defenses. Learn to identify and exploit misconfigurations in tens of the most used GCP services. Master specialized Red Team and Whitebox tactics tailored for GCP, enhancing your ability to detect and correct complex security flaws. Moreover, gain insights into red teaming within Google Workspace and discover effective strategies for pivoting between GCP and Google Workspace platforms.
![]() Beginning from foundational principles master your expertise in Azure and EntraID security. Learn to spot and exploit misconfigurations in Azure and EntraID services. Master red teaming and whitebox tactics tailored for these platforms, enabling you to tackle complex security vulnerabilities. This certification course aims to elevate security professionals into specialists in Azure and EntraID security.
Beginning from foundational principles master your expertise in Azure and EntraID security. Learn to spot and exploit misconfigurations in Azure and EntraID services. Master red teaming and whitebox tactics tailored for these platforms, enabling you to tackle complex security vulnerabilities. This certification course aims to elevate security professionals into specialists in Azure and EntraID security.
![]() Beginning from foundational principles master your expertise in Azure and EntraID security. Learn to spot and exploit misconfigurations in Azure and EntraID services. Master red teaming and whitebox tactics tailored for these platforms, enabling you to tackle complex security vulnerabilities. This certification course aims to elevate security professionals into specialists in Azure and EntraID security.
Beginning from foundational principles master your expertise in Azure and EntraID security. Learn to spot and exploit misconfigurations in Azure and EntraID services. Master red teaming and whitebox tactics tailored for these platforms, enabling you to tackle complex security vulnerabilities. This certification course aims to elevate security professionals into specialists in Azure and EntraID security.
![]() Beginning from foundational principles master your expertise in Azure and EntraID security. Learn to spot and exploit misconfigurations in Azure and EntraID services. Master red teaming and whitebox tactics tailored for these platforms, enabling you to tackle complex security vulnerabilities. This certification course aims to elevate security professionals into specialists in Azure and EntraID security.
Beginning from foundational principles master your expertise in Azure and EntraID security. Learn to spot and exploit misconfigurations in Azure and EntraID services. Master red teaming and whitebox tactics tailored for these platforms, enabling you to tackle complex security vulnerabilities. This certification course aims to elevate security professionals into specialists in Azure and EntraID security.
![]() Do you know how the AWS CLI can be weaponized? In this post I explain how I abused the Aliases feature to achieve persistence.
Do you know how the AWS CLI can be weaponized? In this post I explain how I abused the Aliases feature to achieve persistence.