eCPPTv2 All you need to know

Hello!. In today’s post, we are going to talk about the eLearnSecurity eCPPTv2, which I have recently passed.
I’m going to talk you about my experience during the certification process, how to prepare for the certification and some tips which will be useful if you are thinking of becoming certified.
This is not going to be a long post, but I am sure it will be of great use to you.
About eCPPTv2
The certification voucher costs 400$ and can be purchased here, if is too expensive for you, you may be able to get it cheaper on specific dates like black Friday or Christmas.
Into eLearnSecurity webpage we can see the following image:
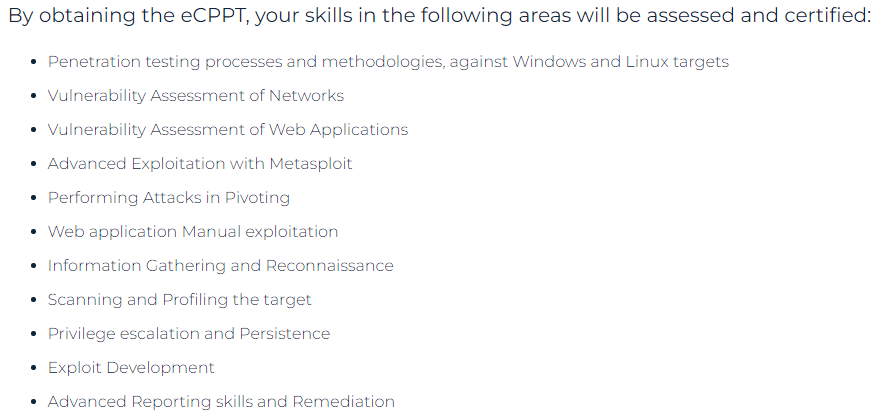
I can confirm that all of the above are necessary to pass the exam, even if you use metasploit as the main tool during the exam.
eCPPTv2 is well known because is a certification focused on pivoting and stack based buffer overflow, but pivoting is the main technique you must master in order to pass the exam, practice a lot of pivoting before you start your certification process.
The Certification Process
This is a chronological summary of what my exam was like:
1st Day:
Whenever I have a certification, I like to get up early and this was no different, at 8am I was starting my exam.
Don’t tell me why, but I always have problems with the VPN files (This was not eLearnSecurity fault), my Kali Linux Virtual machine has the latest version of OpenVPN, and the file provided by eLearnSecurity is made to work with an older version of this software. If this happens to you, don’t worry, you only need to change one line from the .ovp file from Ciphers to Data-Ciphers and the file will work, but this got me nervous for 15 minutes, till I realized the error.
Once I solved the problem and I had connectivity, I read the letter of engagement carefully multiple times, and started to run my firsts nmap scans.
This certification is not like a CTF, you need to report all the vulnerabilities you are able to find during the environment penetration phase, so don’t think about getting a shell and done.
I had some trouble trying to identify the vulnerability presented in the first target, but after some time researching I got a foothold into it, I never exploited this vulnerability before, but if you have done your training, won’t be any issue, remember, in this exam, enumeration is the key.
After exploiting this first host, I discovered new hosts and performed pivoting to them.
I was able to complete the 60% of the exam on the first day, so I went to sleep happy, knowing I had 6 days left to finish the penetration phase.
2nd Day:
I didn’t sleep too much cause I was thinking about the exam and how to continue, but getting a rest is always good.
Was time to face the Buffer Overflow target, I was confident because I trained a lot my buffer overflow technique, but this is one of the critical parts of the exam, where most people get stuck for days.
I had my Windows 7 32 bit machine ready to test the application, and after some time creating my payload, I was able to exploit the buffer overflow vulnerability on the first try.
Took me 2 hours more or less to realise how to continue with the exam, and after enumerating like hell, I was able to discover the host located in the last network mentioned in the letter of engagement gaining access to it.
I need to say that the last host was the most CTF based, I needed to perform Privilege Scalation and root the machine, once I was root I realised that I had pawned the entire Network requested in the letter of engagement, this was an awesome feeling, but the exam is not only about getting a shell in every host like I said before.
3nd Day:
So I had 4 days left before I needed to start my report, I spent this entire day looking for new vulnerabilities in the hosts I had already compromised, and trust me, there are more, I used several scanners in every host and perform my pillaging phase, saving everything for the report.
4th and 5th Day:
I started my report, I didn’t use any automated software, just Google Docs.
I was calm cause I had more than one week to write the report, trying to include everything I had discovered and explaining everything in depth, to show that I understand everything I have done, you should do the same.
I have never done a report before, but in the letter of engagement, you are told what your report has to include for it to be valid, you can stick to these requirements or you can use a more professional template that you can find on the internet.
At the end, the report took me 106 pages, but don’t worry if your’s is shorter, there is not page minimum or maximum.
At the end of the day I uploaded my report to eLearnSecurity Webpage.
Conclusion
I had 9 days left when I uploaded my report, you have more than enough time to make the exam (7 days access to the laboratory and 7 days to write the report).
Don’t worry about that, take your time and try no to go fast, you will miss a lot of vulnerabilities which will be needed for your report.
Take breaks to rest when you are tired, I used to stop for exercise and go outside for a while when I was tired.
Don’t overthink too much if you get stuck, the vulnerabilities are not hard and if something is not working and you are sure that you are not wrong, reset the lab, sometimes is unstable, I reset my lab 5 times before finishing the exam, but you may not need it.
The truth is that it has been an exam that I have enjoyed very much, it requires you to have the knowledge to be able to pass, otherwise you will not overcome certain phases of the exam.
Training & Tips
I recommend the INE training course for this certification, which can be found in this link, this course will teach you almost everything you need to know to take the exam.
INE trainings are more focused on Metasploit Framework, in my case, I made the exam without Metasploit, only using Chisel and Sockat as Pivoting Tools, but if you use Metasploit, everything will be easier.
It doesn’t matter what tools you use during the exam, but I recommend that you practice with some beforehand and use your own methodology, otherwise, it is quite likely that you will end up getting confused and switching to tools you have never used before.
This is the study path I recommend to pass the exam:
1. INE Penetration Testing Professional Course.
Is not required to complete all the modules, I did it and I recommend it, but the main ones are:
- Penetration Testing: System Security.
- Penetration Testing: Network Security.
- Penetration Testing: Web App Security.
2. TryHackMe Wreath Network. Link
You will learn new ways and tools to perform and practice pivoting.
3. TryHackMe Offensive Pentesting Path (Buffer Overflow Exploitation).

Complete all the machines, even repeat them if necessary until you are confident.
4. TryHackMe Blue. Link.
5. TryHackMe 0day. Link.
6. Create your own pivoting environment with a Buffer Overflow Machine, if you don’t know how to do it, you can check my VMware Post here.
If you complete these steps, I’m pretty sure that you will pass the exam with no issue.
Hope to see you certified soon!. Slayer 05/05/2023