Stealing Cookies via XSS
 Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user.
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user.
 Link-Local Multicast Name Resolution (LLMNR) and NetBIOS Name Service (NBT-NS) are two name resolution services that Windows machines use to identify host addresses on a network when DNS resolution fails. LLMNR and NetBIOS are enabled by default on modern Windows computers.
Link-Local Multicast Name Resolution (LLMNR) and NetBIOS Name Service (NBT-NS) are two name resolution services that Windows machines use to identify host addresses on a network when DNS resolution fails. LLMNR and NetBIOS are enabled by default on modern Windows computers.
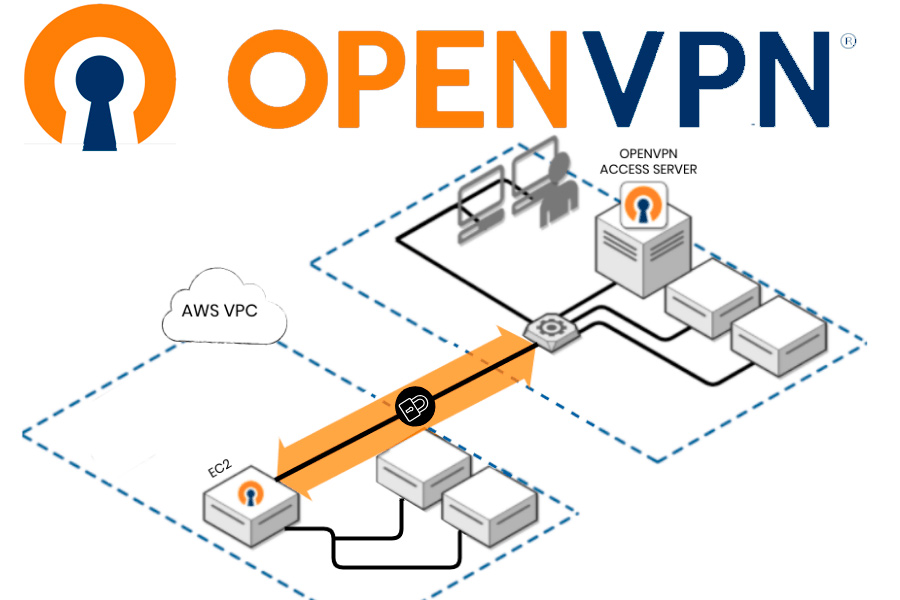 OpenVPN is a free software-based connectivity tool: SSL, VPN Virtual Private Network. OpenVPN offers point-to-point connectivity with hierarchical validation of remotely connected users and hosts.
OpenVPN is a free software-based connectivity tool: SSL, VPN Virtual Private Network. OpenVPN offers point-to-point connectivity with hierarchical validation of remotely connected users and hosts.
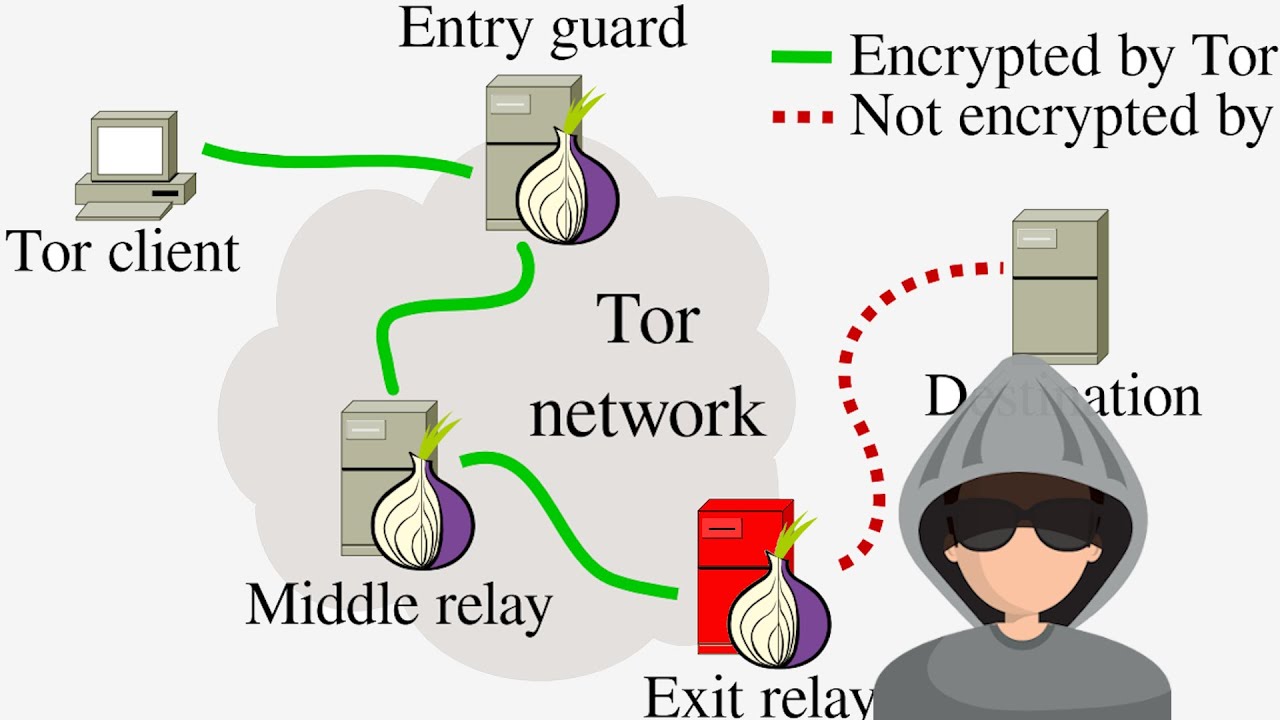 The Tor network depends on volunteers who donate bandwidth. The more people keep repeaters running, the Tor network will be better. Today’s Tor network is quite small compared to the number of people who need to use it, which means we need more volunteers like you to launch repeaters.
The Tor network depends on volunteers who donate bandwidth. The more people keep repeaters running, the Tor network will be better. Today’s Tor network is quite small compared to the number of people who need to use it, which means we need more volunteers like you to launch repeaters.
 Whonix is an operating system that utilizes top level security research and best practices to help users stay anonymous on the internet. To protect a user’s anonymity on the Internet on the technological level Whonix uses virtualization and the Whonix-Workstation combined with the Whonix-Gateway to force all connections through the Tor network.
Whonix is an operating system that utilizes top level security research and best practices to help users stay anonymous on the internet. To protect a user’s anonymity on the Internet on the technological level Whonix uses virtualization and the Whonix-Workstation combined with the Whonix-Gateway to force all connections through the Tor network.
 The eLearnSecurity Junior Penetration Tester (eJPTv2) is a 100% practical certification on penetration testing and information security essentials. By passing the exam, a cyber security professional proves to employers they are ready for a rewarding new career.
The eLearnSecurity Junior Penetration Tester (eJPTv2) is a 100% practical certification on penetration testing and information security essentials. By passing the exam, a cyber security professional proves to employers they are ready for a rewarding new career.
 Proxychains-ng is a proxy server that supports HTTP, SOCKS4 and SOCKS5 internet protocols, and that works on Linux / GNU, BSD and Mac OS X distributions. Proxychains-ng allows any TCP connection made by a given program to follow a series of proxies up your destiny. In today’s post, we are going to cover the installation, configuration and usage of proxychains in kali linux.
Proxychains-ng is a proxy server that supports HTTP, SOCKS4 and SOCKS5 internet protocols, and that works on Linux / GNU, BSD and Mac OS X distributions. Proxychains-ng allows any TCP connection made by a given program to follow a series of proxies up your destiny. In today’s post, we are going to cover the installation, configuration and usage of proxychains in kali linux.

 You have been assigned to a client that wants a penetration test conducted on an environment due to be released to production in seven days. The client requests that an engineer conducts an assessment of the provided virtual environment. The client has asked that minimal information be provided about the assessment, wanting the engagement conducted from the eyes of a malicious actor (black box penetration test). The client has asked that you secure two flags (no location provided) as proof of exploitation.
You have been assigned to a client that wants a penetration test conducted on an environment due to be released to production in seven days. The client requests that an engineer conducts an assessment of the provided virtual environment. The client has asked that minimal information be provided about the assessment, wanting the engagement conducted from the eyes of a malicious actor (black box penetration test). The client has asked that you secure two flags (no location provided) as proof of exploitation.

 ¡Welcome to my webpage! Amazing things are about to come.
¡Welcome to my webpage! Amazing things are about to come.