Whonix - Networking

Whonix is a Kicksecure–based security hardened Linux distribution. Its main goals are to provide strong privacy and anonymity on the Internet.The operating system consists of two virtual machines, a “Workstation” and a Tor “Gateway”, running Debian GNU/Linux. All communications are forced through the Tor network.
In this post, I’m going to cover the installation and configuration of whonix, which is in my opinion, the best way to route your traffic through the Tor network. Whonix creates a network in which all the traffic generated is anonymized, is pretty useful for pentesting, cause we don’t need to configure our machines in order to access the Tor network, Whonix gateway will do it for us.
If you want to know how Tor Networks and Proxy Server works check out my Proxychains post.
All you need to know
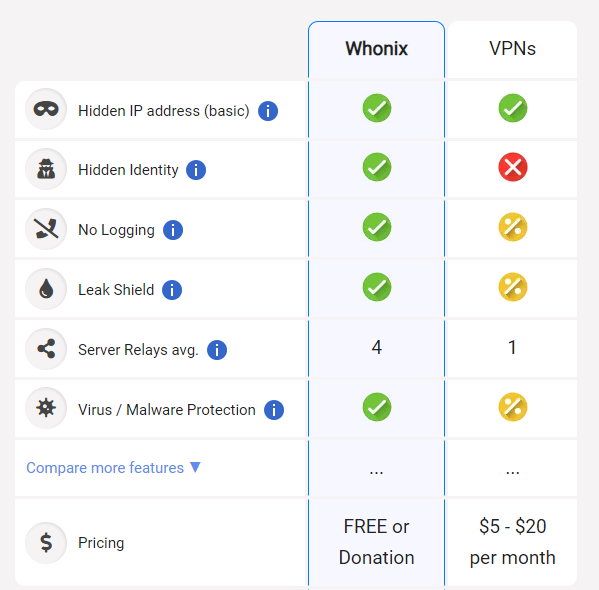
Whonix is the most watertight privacy operating system in the world that runs like an app in your host operating system. If a web browser (or any application) is running inside Whonix however the user’s IP address is still protected even if the browser has an IP leak bug or if the browser has been compromised by malware. This is not a theoretic consideration. This has happened in the past.
VPNs are usually faster than Tor, but they are not anonymous networks.
VPN administrators can log where a user is connecting from and the destination website, breaking anonymity in the process. Promises made by VPN operators are meaningless, since they cannot be verified to be truthful and can be broken at any time, anyway you can use VPNs and Whonix simultaneously in order to increase the security level if you wish.
Whonix supports the following OS and virtualization services, by configuring the gateway we will be able to use our Windows or Linux machines to route the traffic through the Tor network.
As we can see in the following picture, Whonix is more than a Tor node, also implements a firewall system combined with malware protection.
You can download whonix for free in the following link.
Installation & Configuration
I’m going to be using VirtualBox in this example, cause is the default installation method.
By accessing the following link we can download de Vbox image, we have 2 versions (CLI/Xface) I’m going to be using the Xface one in order to be able to configure everything from the graphical interface.
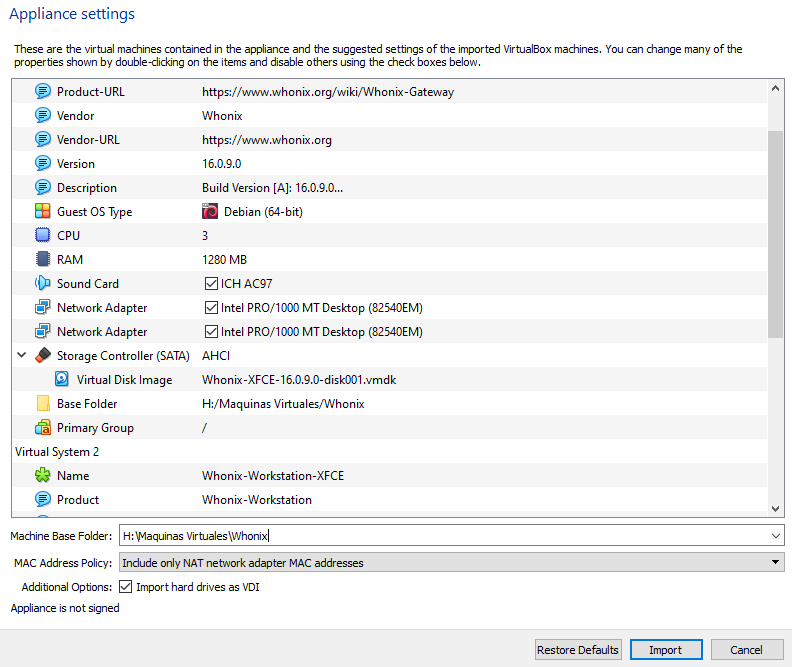
One we downloaded the .ova file, we import it into virtual box, you can add more ram to the machine if you wish, but I’m going to leave it as default configuration suggests.
Once the import is completed, we will see 2 new machines on our VBox, the Whonix Gateway and the Workstation.
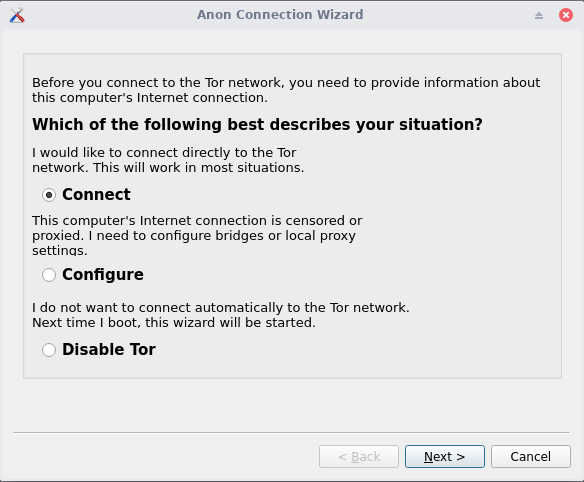
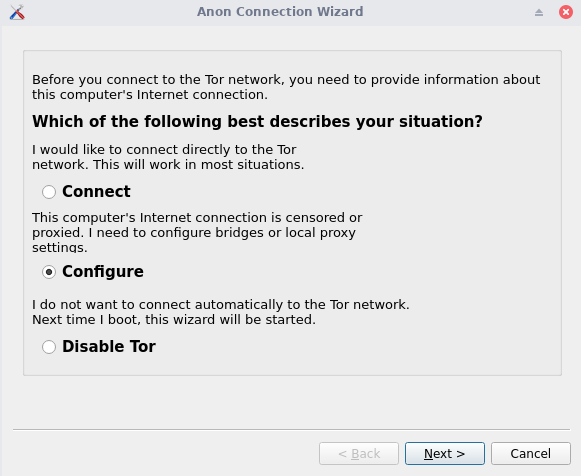
I’m going to power up both and start with the configuration, accept the text box which appears on boot in both machines. In the Gateway one, a pop will appear with the setup, in this setup we can chose between using Tor, disable Tor or adding our own proxies or bridges, we will cover this later, now just select connect to start using Tor chain.
Whonix gateway will start to configure Tor, just wait till it finishes and select Finish.
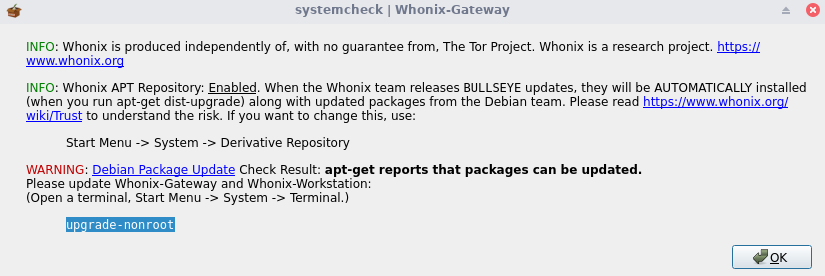
I got this warning which tells us to update the packages, so we open a terminal and type the command upgrade-nonroot and reboot when finishes, you may not have this problem.
The final result in both machines should be with every field showing in green.
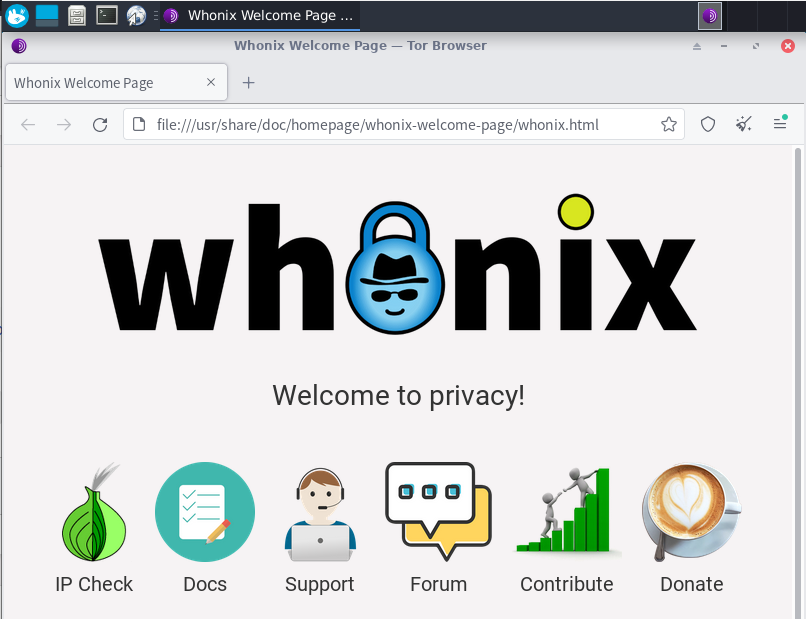
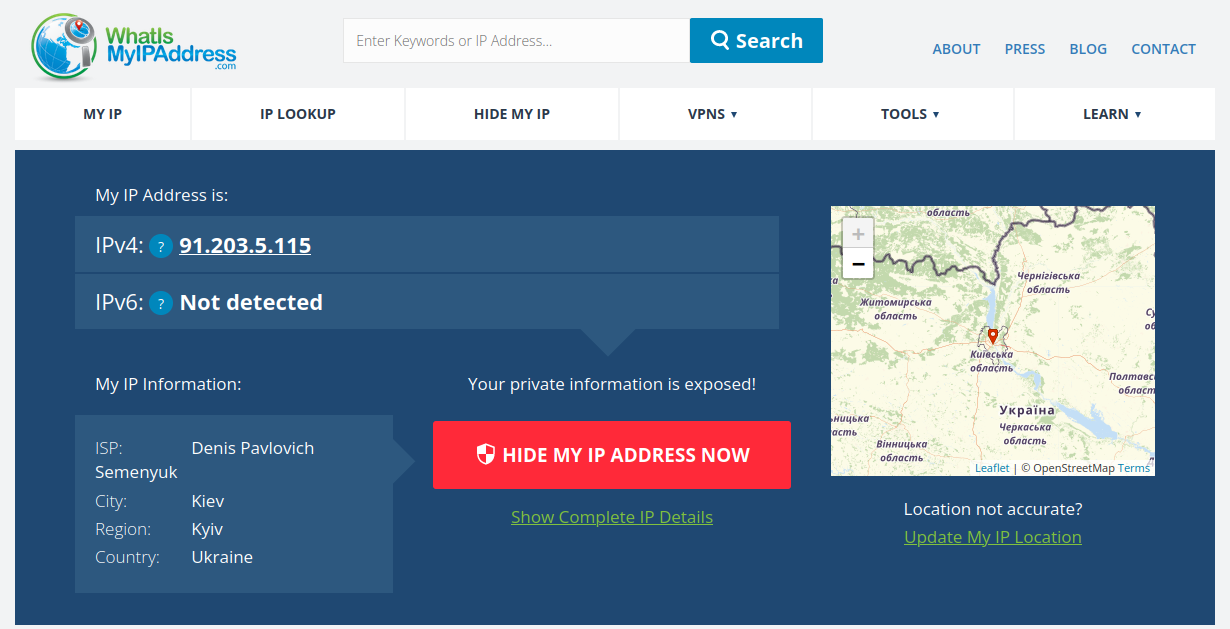
If you followed the steps, now you should be able to open the web browser into the Workstation machine and click on IP Check (The gateway needs to be running always, if not you won’t have connectivity).
After clicking into the IP Check we get the Tor network connectivity confirmation and our Tor IP address, you can browse into an IP geolocalization webpage and you will see that is not able to track your location.
The workstation is preconfigured to work with the Whoninx Gateway, but the good thing about Whonix is that we can use any kind of the supported SO we have seen, so let’s configure a new Kali Linux machine and tunnel our traffic to the Whonix Gateway.
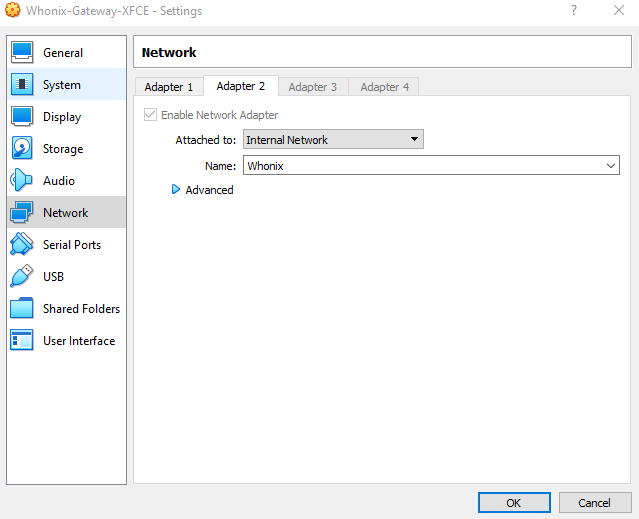
If we check the Whonix Gateway configuration, we can see, that creates an internal network called Whonix, this network is preconfigured into the workstation, but we can add any host to it and use it as a gateway.
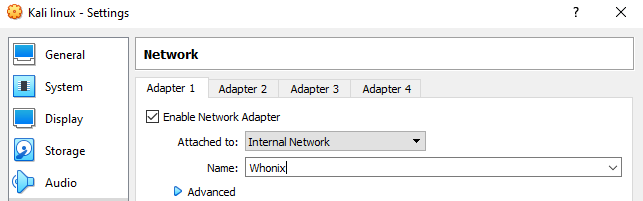
We just need to set up the internal network into our Kali Linux machine.
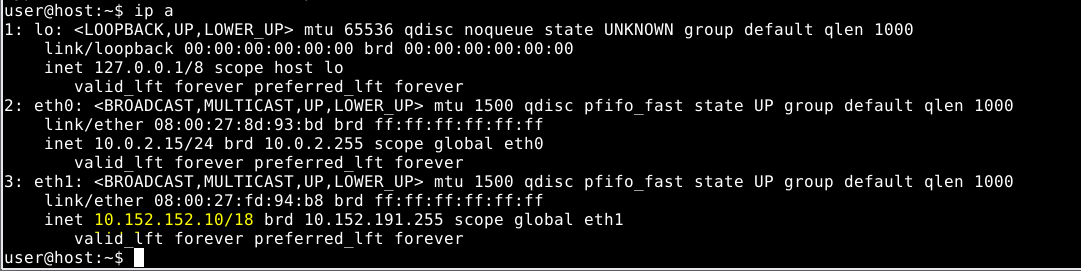
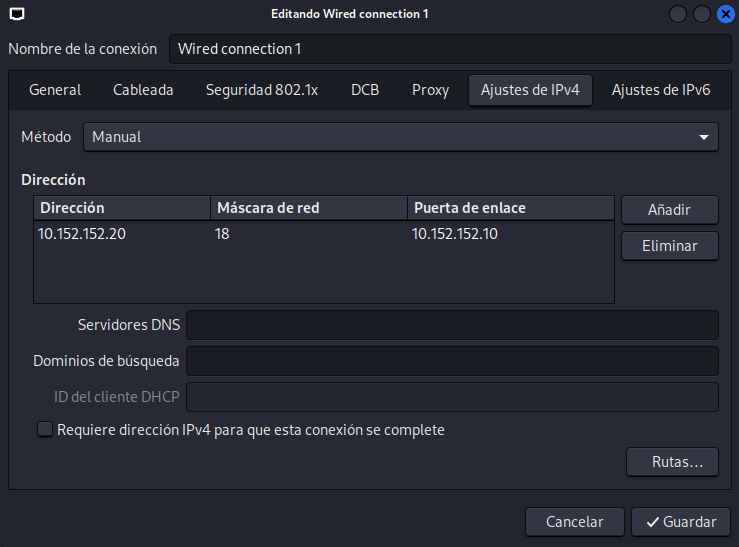
Once we have this, we need to check the Whonix Gateway internal ip address by executing ip a in the terminal, take note of the IP and subnet mask.
And configure the gateway into the Kali Linux interface, set a valid IP address from the internal network range, and be aware of the /18 subnet mask which is 255.255.192.0 in decimal notation, this may change in your case.
Once we have this, all your network traffic will be routed via the Whonix Gateway (Tor Network), you can confirm this by browsing an IP geolocalization webpage.
But there’s one problem with this method, most of the web pages and web browsers, knows which IP addresses are from Tor network and blocks them, also in some countries, Tor network is forbidden by the government.
In the following section, I’m going to show you how to bypass these restrictions, I recommend you to do it, you will have a better experience while navigating and executing your tools.
Tor Bridges
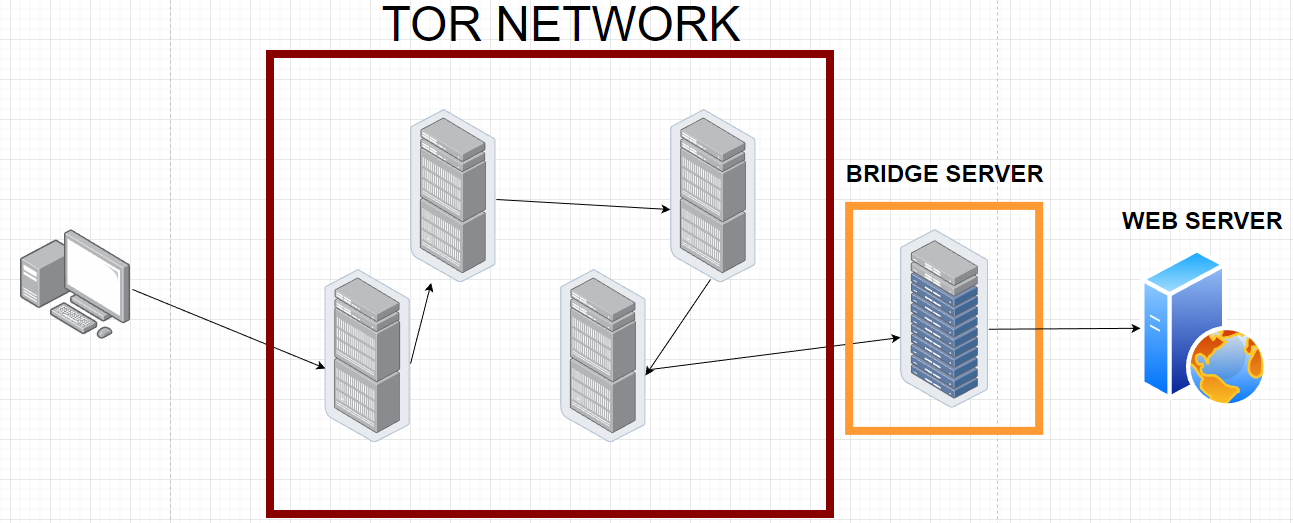
Tor bridges, chains a proxy server as the last hop of our connection, so we no longer have an IP of the Tor network, even though our traffic is being routed through it.
In order to clarify the concept I made this graphic.
Once we know this, let’s configure a Tor Bridge, first of all you need to get a bride into the following link.
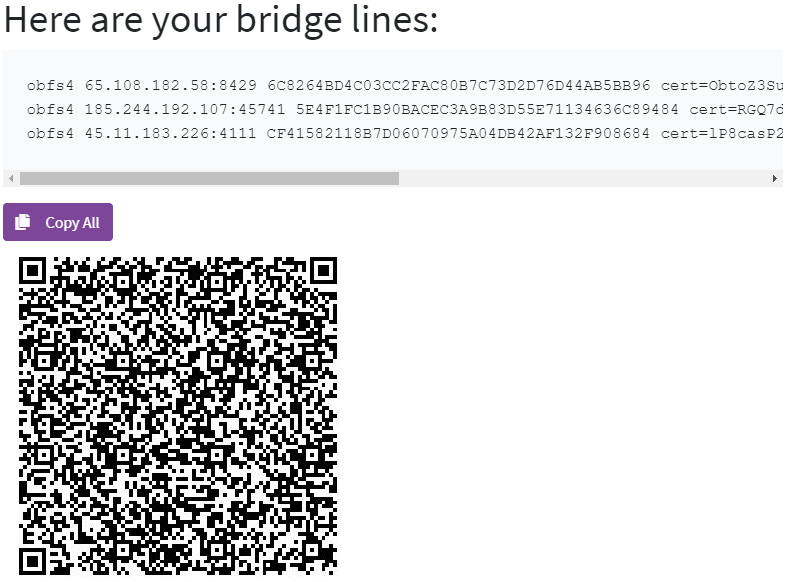
Just select obfs4 and Get Bridges.
As a result, you will receive 3 Tor bridges, copy them all.
Now we need to go back to the Whonix Gateway and execute the setup Wizard again.
Select configure.
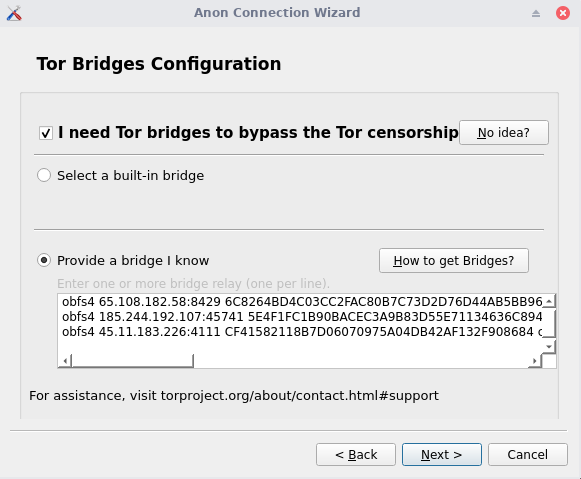
Check the censorship checkbox, select and paste your bridges into the Provide a bridge I know section.
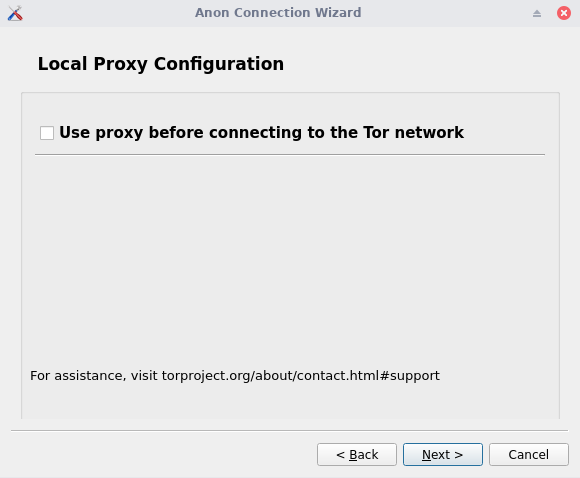
We can also set up a proxy before the Tor network, I’m not going to do it in my case, but you could configure it or use your own VPN service.
We will get a summary and select next to finish, Whonix will reconfigure to start using the bridges you have set, is not necessary, but I recommend you to restart your Whonix Gateway after this.
You will get a new IP address and we will avoid the mentioned restrictions, Whonix Workstation always works better cause is preconfigured to run with the Gateway, but as you can see, we are be able to route the traffic from any virtual machine you want throughout the Tor network with better security in a simple way.
I hope you have learned something new!.